Evacuation Management – Real-Time Safety
Streamlined evacuation and personnel tracking with EntryWise
Safety, clarity, and rapid response are the core strengths of the EntryWise Evacuation Management System, a cutting-edge solution for effective evacuation planning and execution. Designed for industrial facilities, corporate offices, public institutions, logistics centers, warehouses, shopping malls, schools, universities, hospitals, medical centers, hotels, sports and entertainment venues, and critical infrastructure facilities, EntryWise ensures the highest standards of building safety and life protection.
By combining intuitive operation with high operational efficiency, EntryWise gives you complete control over every stage of the evacuation process. Real-time personnel tracking allows security teams and facility managers to respond instantly, minimize risk, and protect people’s lives in any emergency situation.
Fully Automated Evacuation Management
How EntryWise’s Evacuation Management System Works
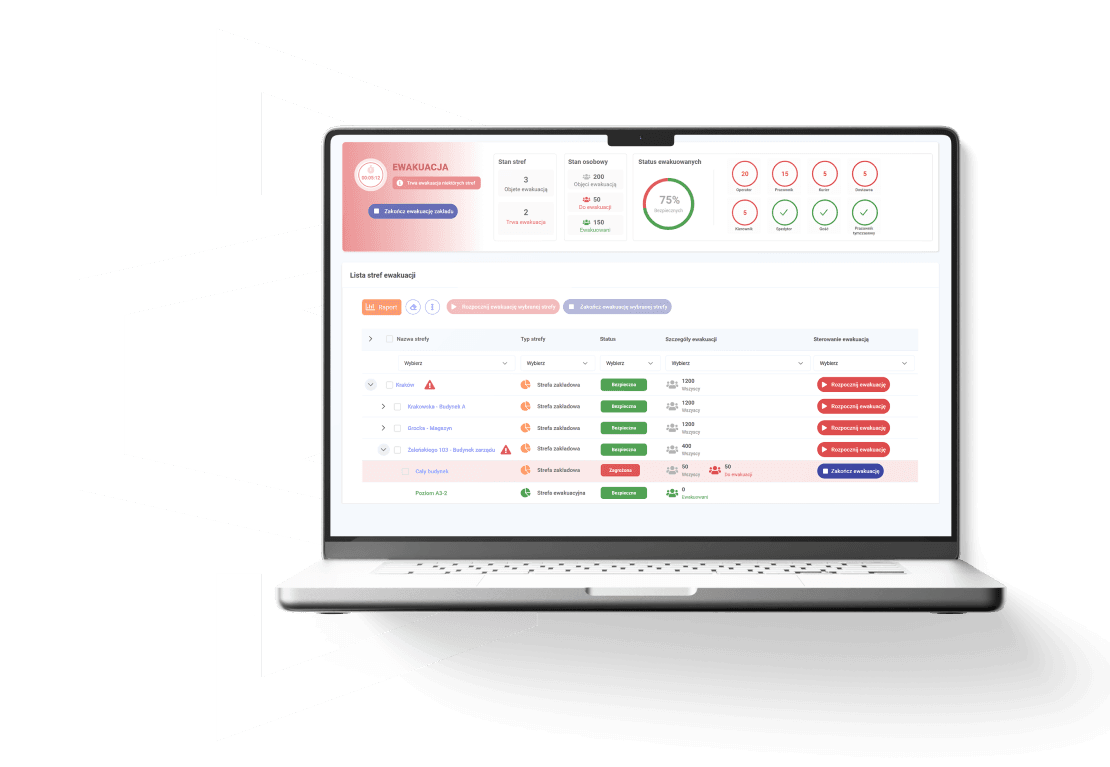
The EntryWise Evacuation Management System significantly enhances building safety and boosts the efficiency of emergency response by delivering precise, real-time monitoring and coordination of evacuation procedures. This advanced safety solution integrates state-of-the-art identification technologies, including proximity cards, RFID key fobs, beacons, and biometric systems, along with access control solutions and dedicated software modules for managing personnel presence and evacuation.
Each individual within the facility is assigned a unique identifier, enabling accurate tracking of their movement across designated safety zones. Operating in real time,the system automatically updates safety status, marking people as "To be evacuated" or "Safe". All information is securely recorded and available to authorized operators, providing full oversight and enabling detailed audits of the entire evacuation process.
The evacuation process can be monitored and managed remotely from any location using a computer, tablet, or smartphone. Powerful search filters and intuitive operator dashboards guarantee full situational awareness and control, even under the most demanding emergency conditions.
Evacuation Management System
EntryWise Features — Built to Protect Everyone in Your Facility
EntryWise provides comprehensive, real-time tools for effective evacuation control:
- Remote and on-site evacuation management - for maximum safety and control
- Real-Time Personnel Monitoring – continuous zone-based tracking for complete situational awareness
- Evacuation Control Panel – central dashboard to coordinate steps and status changes
- Automated Evacuation Alerts – instant notifications for evacuation events and status shifts
- H&S‑Compliant Reporting – generate evacuation, occupancy and personnel reports for audit and review
- Support for Zones and Sub‑Zones – map your building structure and refine control at granular level
- Customisable Occupant Data – personalise occupant profiles and tracking metadata
- Advanced Filtering of People and Zones – quickly drill down on critical elements during incidents
- Integration with Access Control Systems – unify entry data with evacuation management
- Return Configuration After Evacuation – automate re‑entry workflows once the event is cleared
Tailored evacuation workflows
EntryWise enables full customisation of evacuation zones, zone types and return‑assignment rules — aligned with your facility’s structure.
Seamless integration & installation
We deliver complete implementation, integrating with Access Control systems, readers and terminals for harmonised security management.
Real-time evacuation coordination
With our central dashboard, monitor personnel status, assign evacuation markers and manage workflows as events unfold.
Comprehensive system training
We conduct training on zone setup, H&S report generation and configuring system features for optimal use.
Manage from anywhere and maximize your organization’s safety
Benefits of remote management for your organisation
Centralised evacuation oversight across multiple sites
Operate and coordinate evacuation events across dispersed facilities via a unified platform — enabling global visibility in real time.Faster decision-making through presence visibility
Live occupancy counts help you make informed decisions instantly — reducing risk and boosting safety in evacuation scenarios.Automated alerts for evacuation events
Clear notifications trigger on initiation, progress and completion of evacuations, including updates on individual and zone statuses — delivered straight to your response team.Advanced H&S-aligned reporting
Produce evacuation, personnel and occupancy reports in PDF, XLS or CSV formats — ideal for audits, compliance and analytics.Robust data protection and compliance
Personal and evacuation data are fully secured under GDPR standards. Complete event histories and logging ensure transparency and accountability.
More than an evacuation management system
Why choose an evacuation management system?
Comprehensive evacuation management system with real-time coordination, legal compliance, and maximum safety for your facility.
Industry-Ready Solution
Who Benefits from EntryWise’s Evacuation Management System?
The EntryWise Evacuation and Personnel Status Management System is designed to meet the safety needs of every industry. It is ideal for industrial manufacturing, corporate offices, healthcare facilities, educational institutions, retail stores, hotels, public sector buildings, warehouses, logistics centers, and sports or cultural venues. The system provides complete control over occupant safety, supports efficient evacuation procedures, and ensures full compliance with occupational health and safety regulations.
STEP-BY-STEP DEPLOYMENT
What does the implementation process look like?
Need more information? Unsure if our solution is right for you?
Frequently asked questions
FAQ
EntryWise offers comprehensive access control functions, including: