Access control
EntryWise – your key to modern access control
Security, efficiency, and intuitiveness define EntryWise. Our electronic access control system is designed for companies and public institutions that prioritize resource protection without compromising operational fluidity. With EntryWise, you gain full control over access and permissions in a simple and effective way.
Security, efficiency, and intuitiveness define EntryWise. Our electronic access control system is designed for companies and public institutions that prioritize resource protection without compromising operational fluidity. With EntryWise, you gain full control over access and permissions in a simple and effective way.
CONVENIENCE AND SECURITY
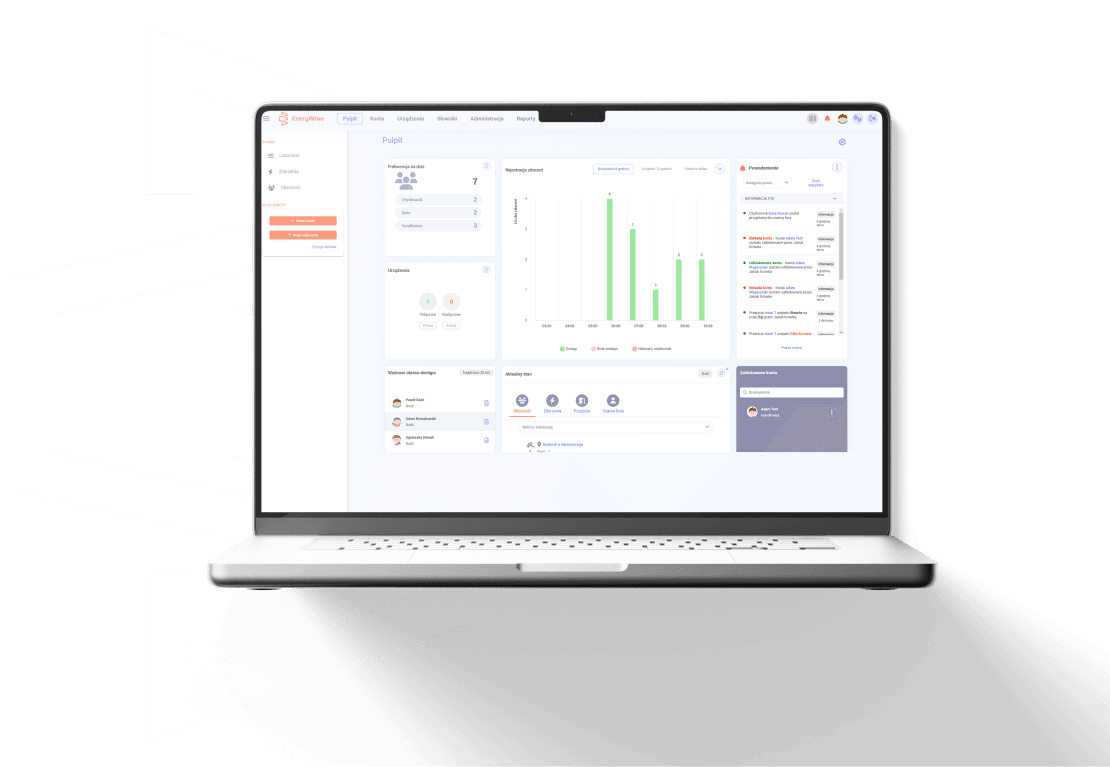
How does access control work?
Modern access control systems enhance security and operational efficiency by enabling precise management of access to specific areas. Our solution integrates advanced technologies such as RFID proximity readers, MIFARE cards, key fobs, and Bluetooth modules. Additionally, access can be authorized via PIN codes, fingerprint recognition, or facial geometry verification.
Each user is assigned a unique identifier—such as a proximity card or key fob—allowing for seamless authentication. The access control system operates in real time, instantly verifying permissions before granting entry to a designated area. Every access attempt is logged, providing administrators with comprehensive monitoring and audit capabilities. With remote management features, access control can be supervised from any location, ensuring full oversight and operational flexibility.
Thanks to its modular architecture, our system is fully adaptable to both office and industrial environments. Designed to meet the highest security standards, it provides a scalable, future-proof solution that aligns with the needs of even the most demanding organizations.
ACCESS CONTROL SYSTEM
EntryWise features – designed to meet your needs
EntryWise provides all the tools you need for effective access management:
- Intuitive assignment of permissions for users and groups.
- Real-time event monitoring and detailed report generation.
- Attendance tracking.
- Overview of employee presence and activity at access points.
- Notifications of desired and undesired events.
- Administrative modules offering quick access to key data.
- Flexible permission assignment and user form creation.
- Encrypted communication between system components.
- Integration with BMS, alarm systems, and more.
Tailored access control solutions
We design access control systems fully customized to your organization's specific security requirements. Our solutions integrate advanced technologies, including RFID proximity readers, biometric scanners for fingerprint and facial recognition, as well as encrypted keypad locks, ensuring seamless security and operational efficiency.
Professional installation services
We provide expert installation of access control devices, including readers, locks, controllers, and other system components. Our installation process ensures optimal performance and seamless integration with your existing security infrastructure.
Access control software configuration
We configure access control software to manage and regulate access to designated areas within your organization. Our solutions provide administrators with full control, enabling real-time event monitoring and seamless security management.
Access control system training
We provide comprehensive training for personnel on the effective use of the access control system. Our training covers credential management, including proximity cards, key fobs, and authentication methods such as PIN codes and biometric verification (fingerprint recognition).
SECURE ACCESS CONTROL
Benefits for your organization
- Efficient multi-location management – EntryWise connects access control devices across multiple sites into a unified system while enabling data isolation where needed.
- Decision-making support – Reports and charts assist managers in analyzing data and making informed decisions.
- GDPR compliance – Protecting personal data and ensuring its integrity are top priorities for EntryWise.
BEYOND ACCESS CONTROL
Why choose EntryWise?
EntryWise is more than an access control system — it’s a partner that supports your organization in overcoming daily challenges:
ACCESS CONTROL SYSTEM
Who is EntryWise for?
Our access control system caters to any industry. From manufacturing and offices to healthcare and education, EntryWise offers flexible solutions tailored to your needs. Industries we serve:
Discover how EntryWise can enhance your organization’s security and efficiency.
Contact us today to choose a modern approach to access management!
STEP-BY-STEP DEPLOYMENT
What does the implementation process look like?
Need more information? Unsure if our solution is right for you?
Frequently asked questions
FAQ
EntryWise offers comprehensive access control functions, including: